Azure Policy
Azure Policy is a service in Azure which allows you create polices which enforce and control the properties of a resource. When these policies are used they enforce different rules and effects over your resources, so those resources stay compliant with your IT governance standard. Through its compliance dashboard, it provides an aggregated view to evaluate the overall state of the environment, with the ability to drill down to the per-resource, per-policy granularity.
Azure Policy uses a JSON format to form the logic the evaluation uses to determine whether a resource is compliant or not.
Policy definition is the conditions which you want controlled. There are built in definitions such as controlling what type of resources can be deployed to enforcing the use of tags on all resources. These are the business rules, described in JSON format.
Policy assignment is the scope of what the policy definition can take effect around. Scope of assignment can be assigned to a individual, resource, resource group or management group. Policy assignments are inherited by all child resources.
Azure Initiative
An Azure initiative is a collection of Azure policy definitions that are grouped together towards a specific goal or purpose in mind. Azure initiatives simplify management of your policies by grouping a set of policies together as one single item. Sometimes also called as Policyset
Assign a Policy
To enforce the Complaince with Azure Policies , we need to assign the policy. In this example, we assign the built-in policy definition called "Allowed locations" to ensure that resources are created in the specific region only.
- Go to the Azure portal to assign policies. Search for and select Policy.
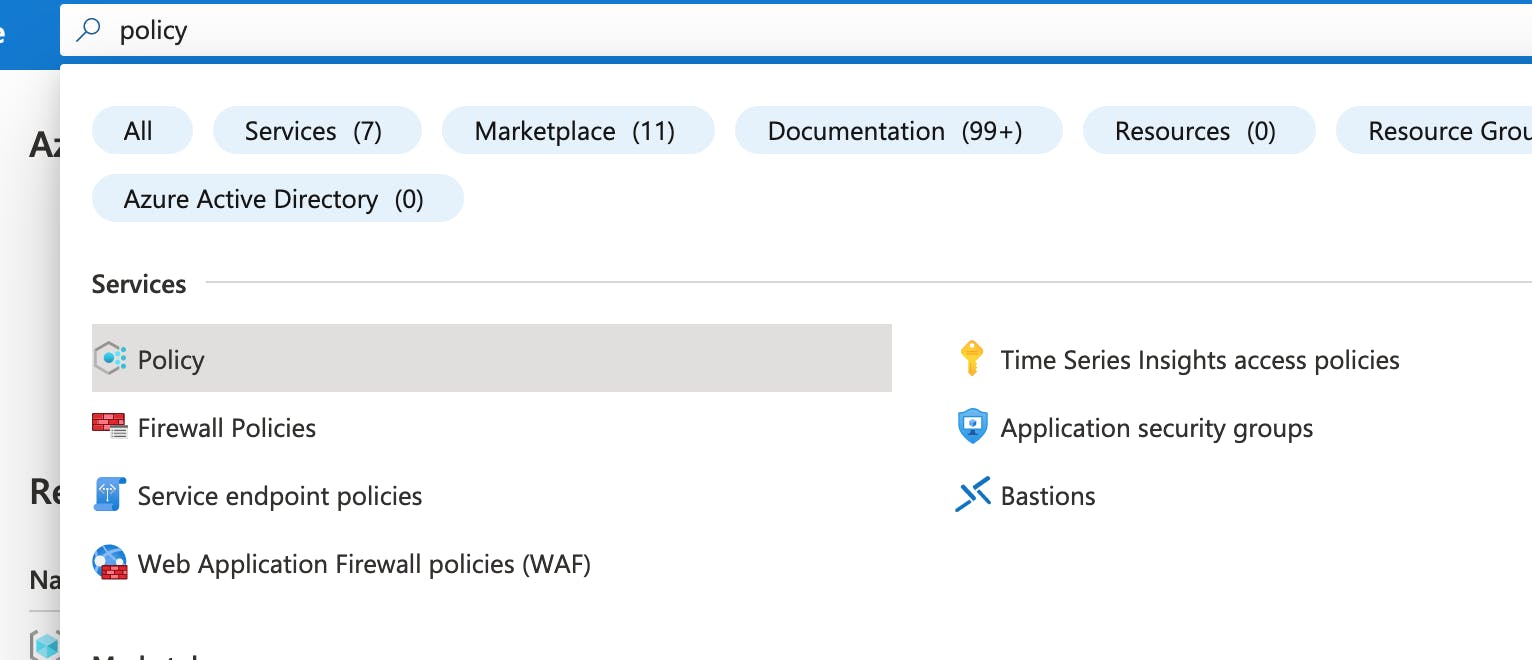
Select Assignments on the left side of the Azure Policy page. An assignment is a policy that has been assigned to take place within a specific scope.
Select Assign Policy from the top of the Policy - Assignments page.
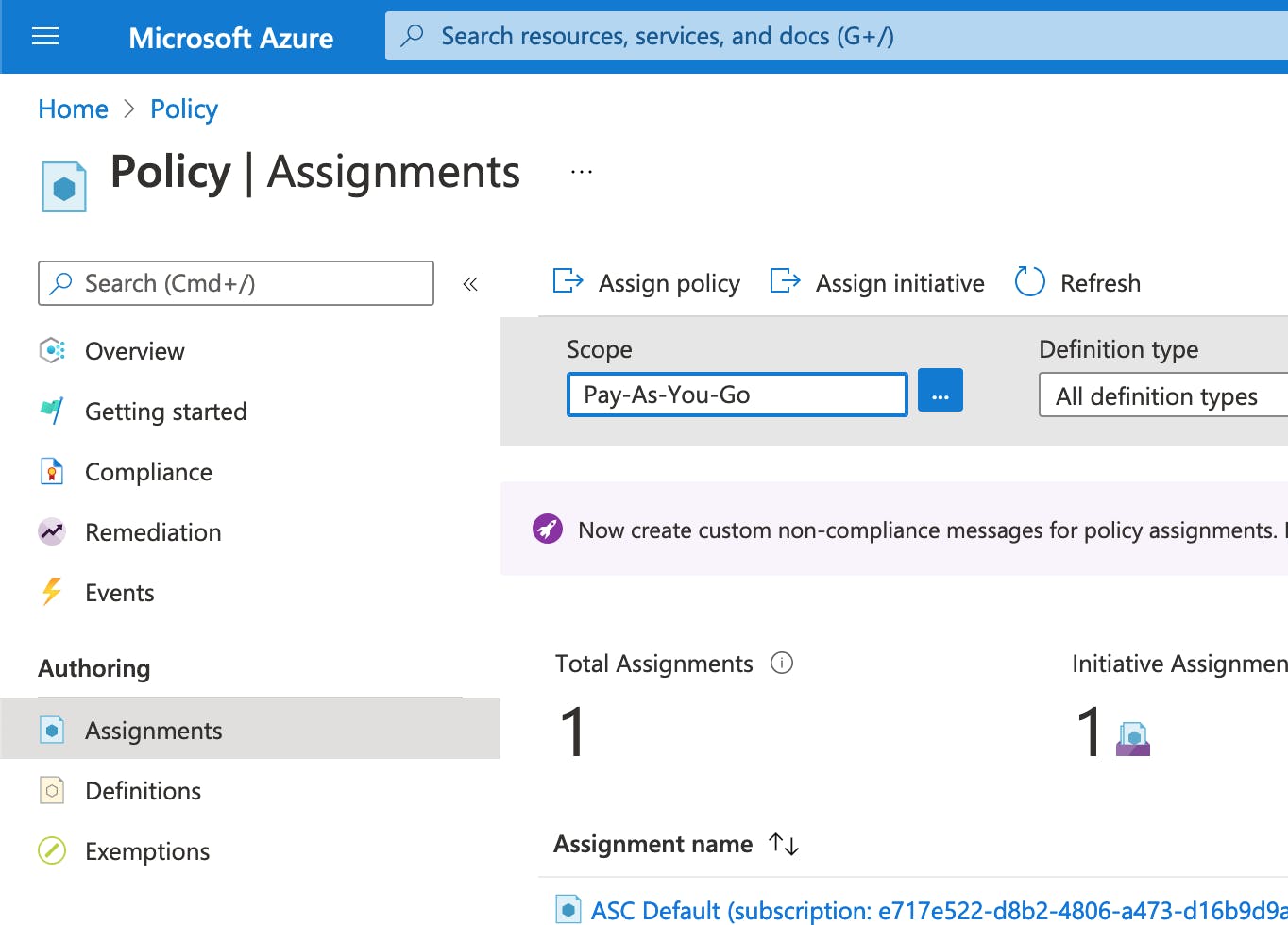
- On the Assign Policy page and Basics tab, select the Scope by selecting the ellipsis and selecting either a management group or subscription. Optionally, select a resource group. A scope determines what resources or grouping of resources the policy assignment gets enforced on. Then select Select at the bottom of the Scope page.
- Resources can be excluded based on the Scope. Exclusions start at one level lower than the level of the Scope. Exclusions are optional.
- Select the Policy definition ellipsis to open the list of available definitions. You can filter the policy definition Type to Built-in to view all and read their descriptions.
- Select Allowed locations. If you it, type locations into the search box and then press ENTER or select out of the search box. Select Select at the bottom of the Available Definitions page once you have found and selected the policy definition.
- The Assignment name is automatically populated with the policy name you selected, but you can change it. Leave Policy enforcement as Enabled.
- Select the Parameters tab at the top of the wizard.
- In the Allowed locations, you need to select the locations in which you want your resources to be created.
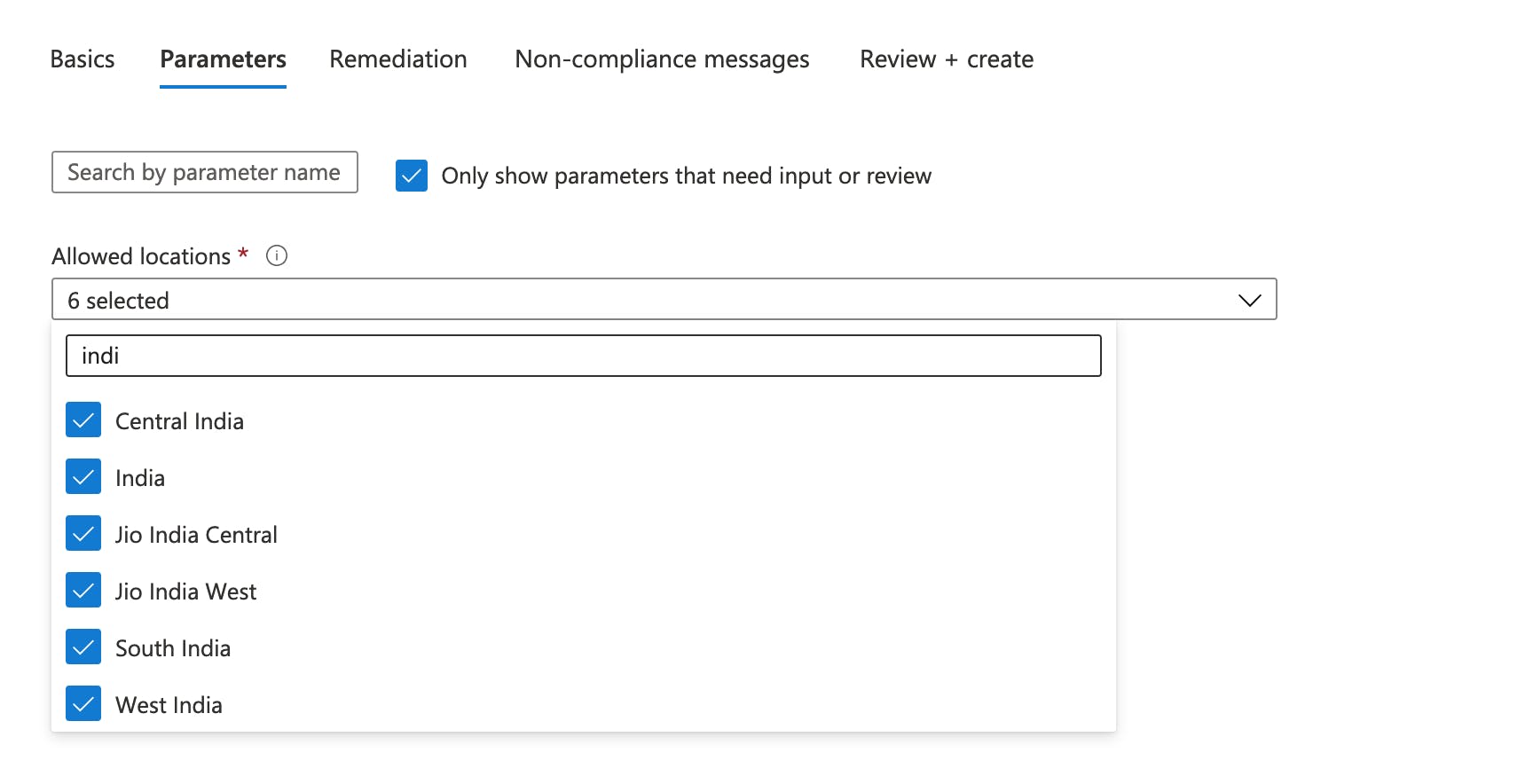
- We will leave the rest of the values as default.
- Select the Review + create tab at the top of the wizard.
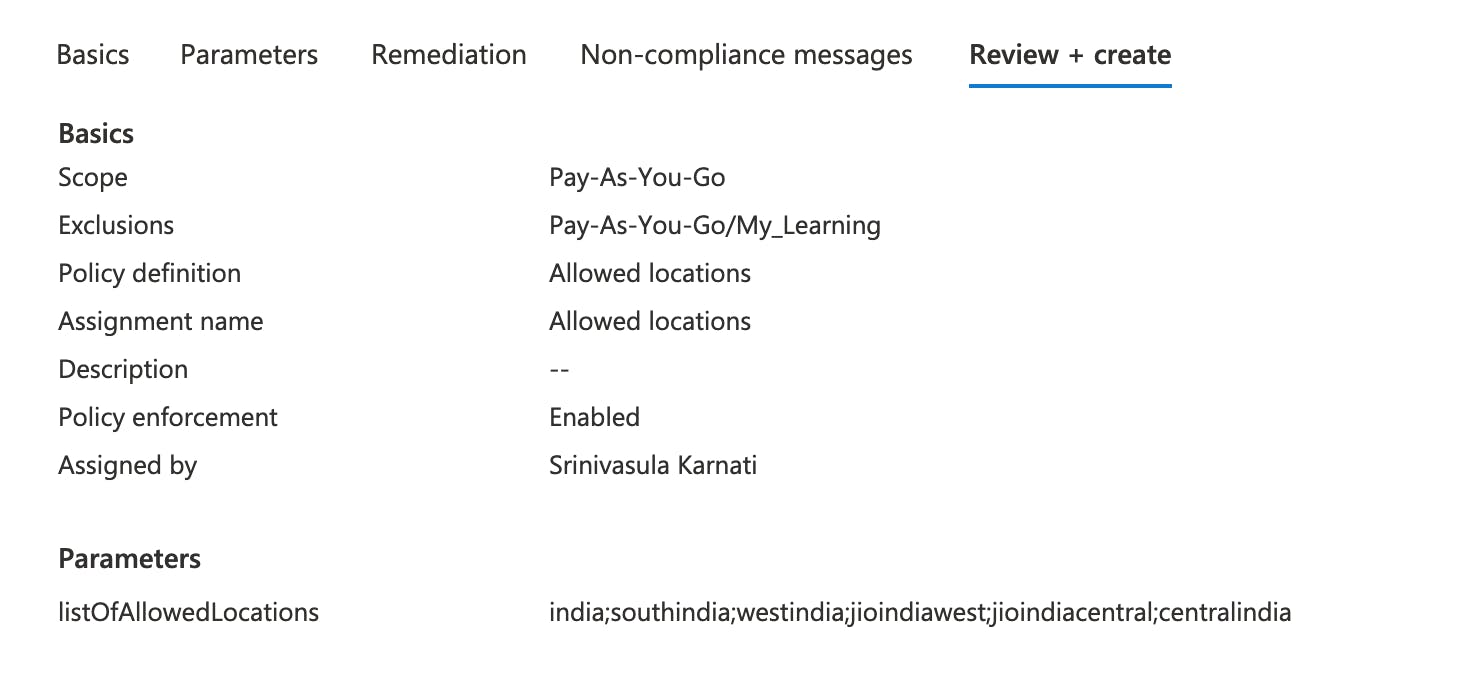
- Review your selections, then select Create at the bottom of the page.
To test our Policy, Let's create two logic apps one in US region and another in India.
- To create a logic apps, click on Add resource -> Search for logic apps
- On the Basics tab, select Your subscription, Resource group, Region (here I selected South India).
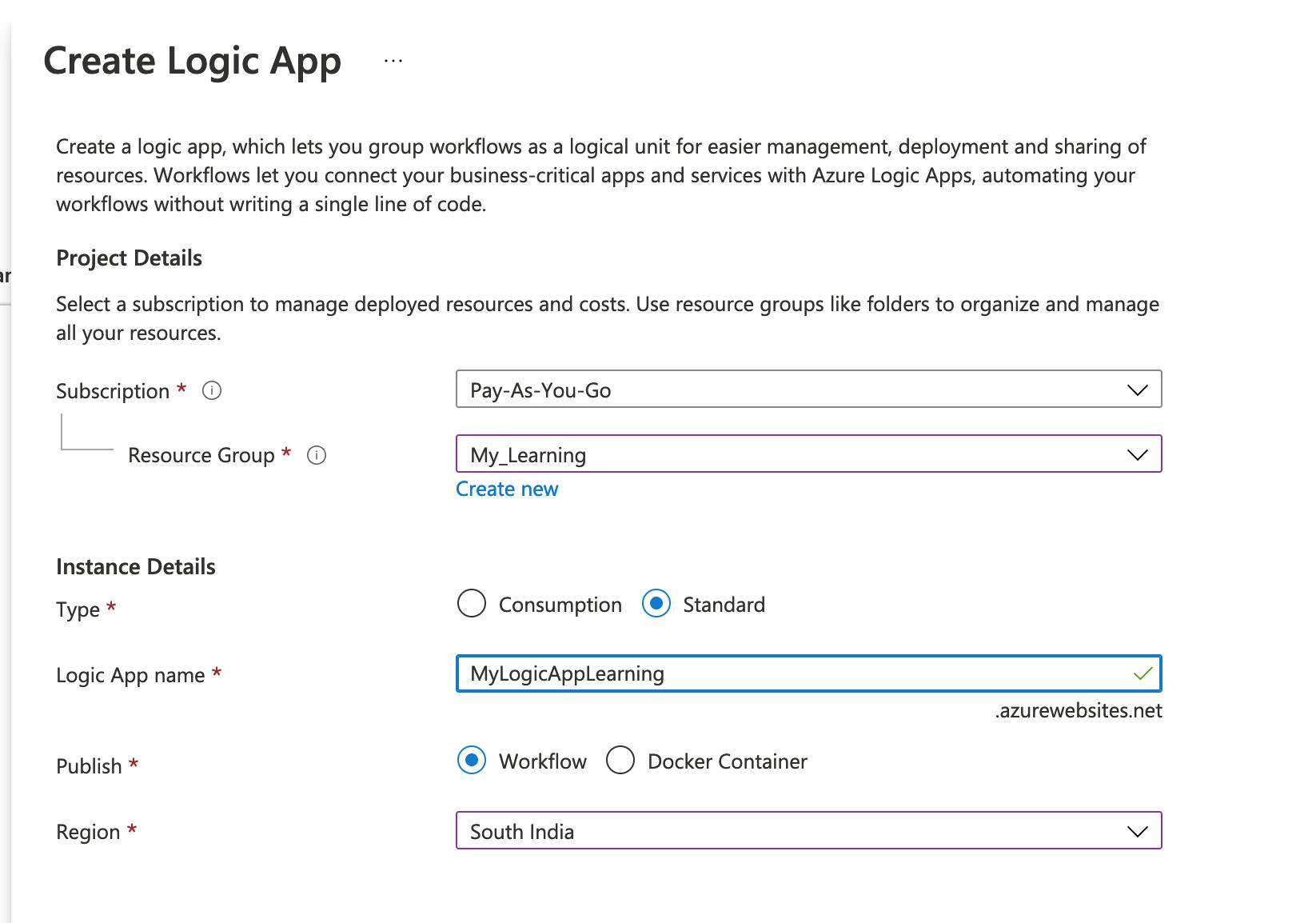
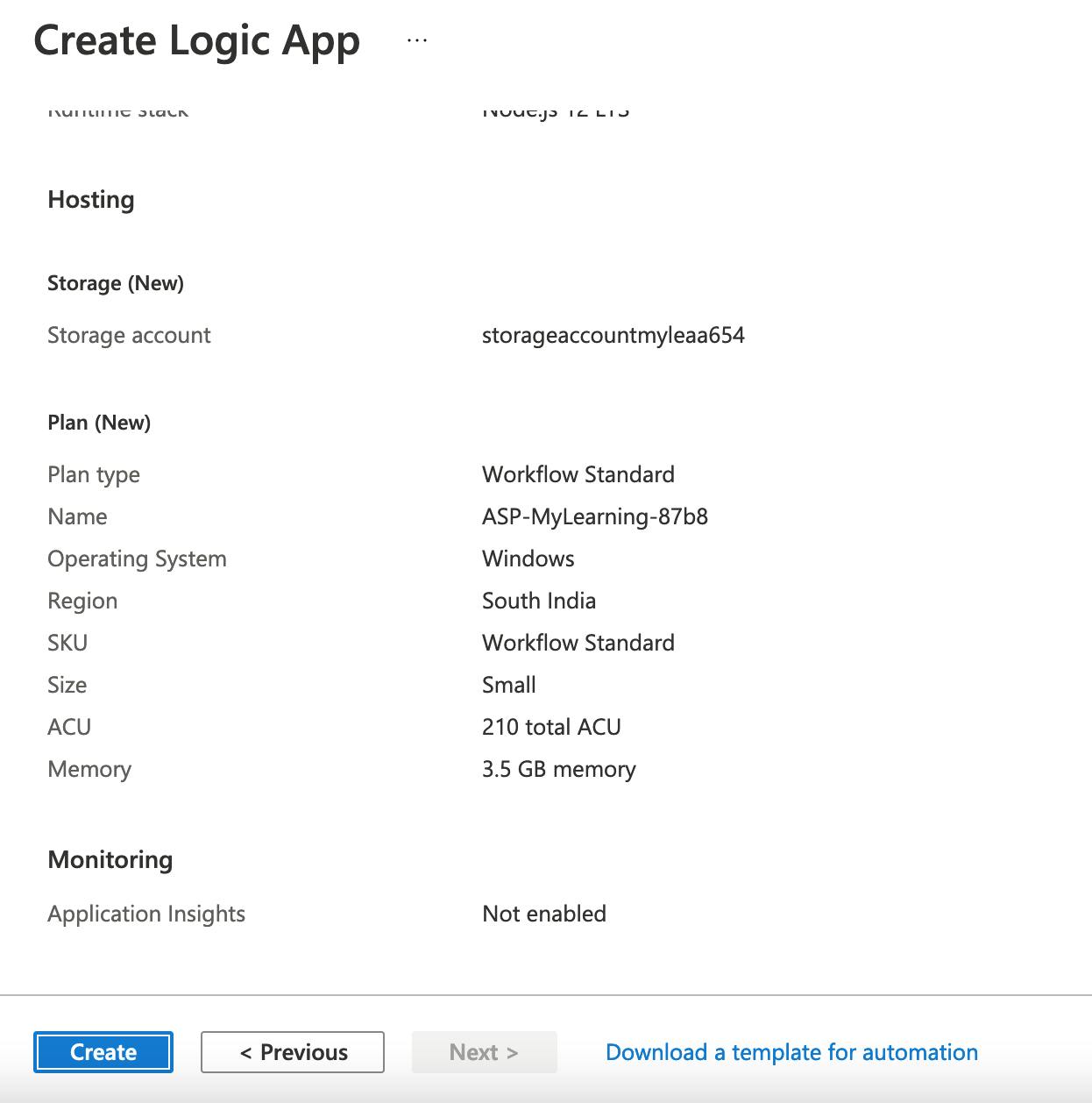
- I will leave all the remaining details as default, We will review and create the Logic app.
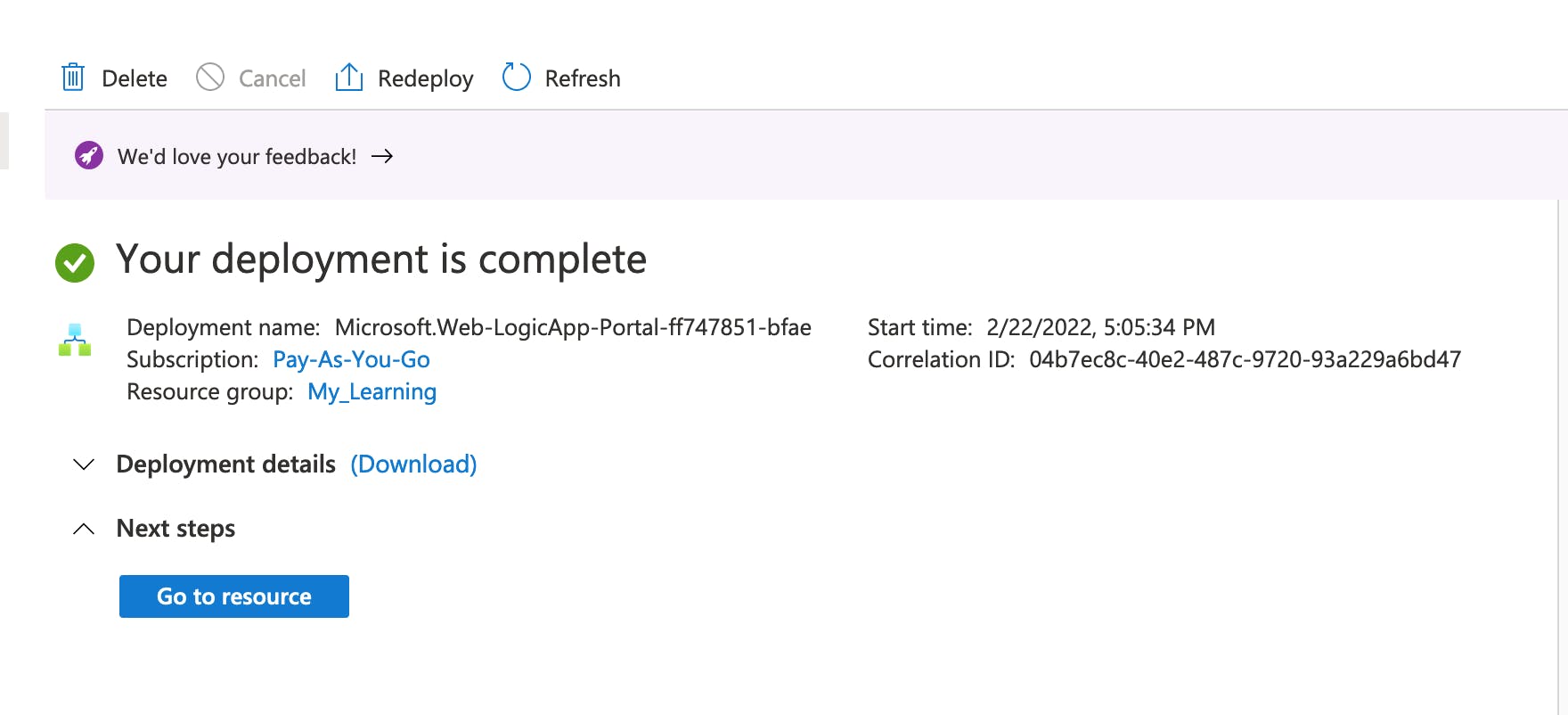
- As you can see the deployment is completed.
- Repeat the same for the US region, the details of resource are as follows
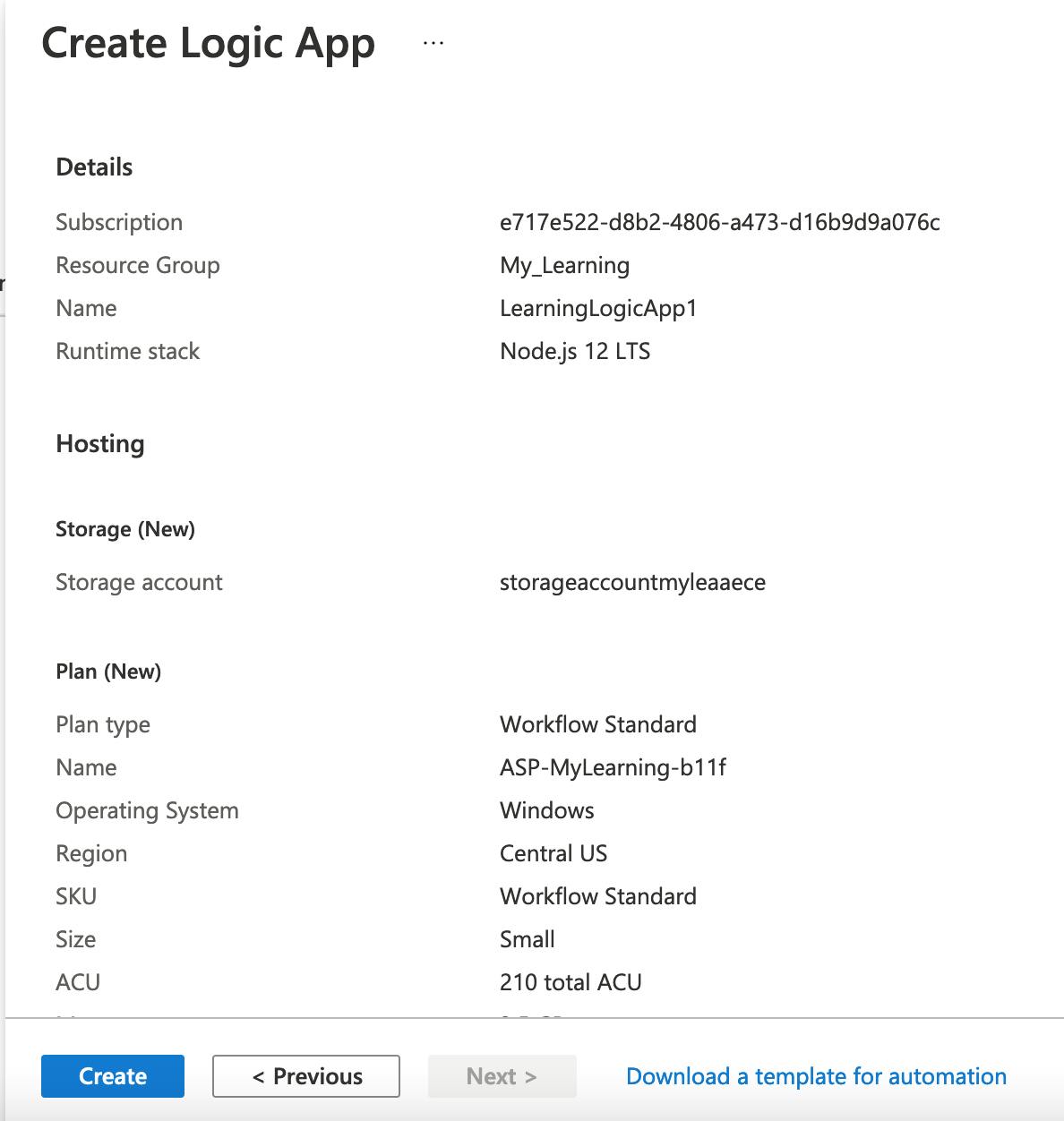
- Though it is not allowed in Policy Definition, validation will be successful.
- Let's try to deploy the resource.
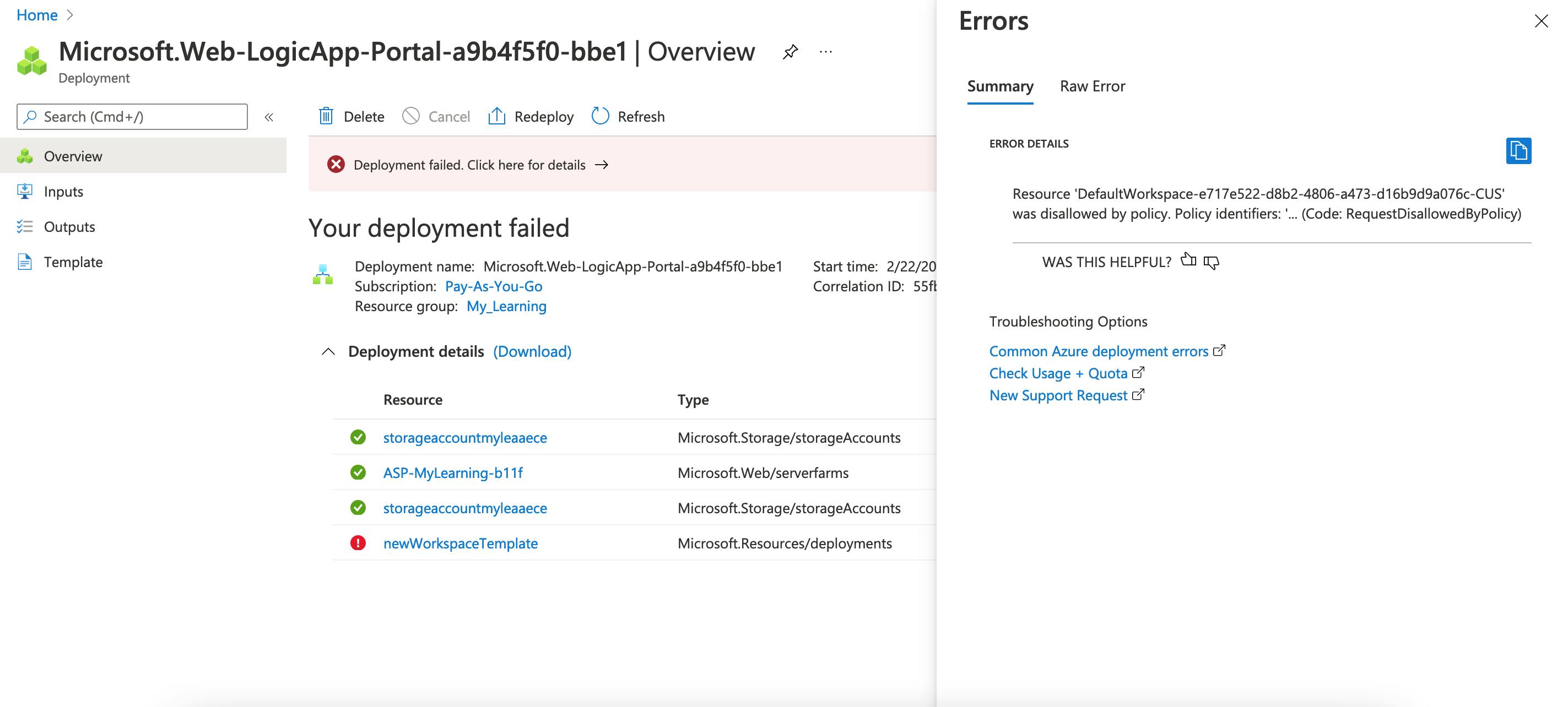
- As you can see the Deployment is failed due to "Disallowed by the Policy".
